SENSOR
Network never lies

AT THE FRONTLINE OF YOUR ATTACK SURFACE
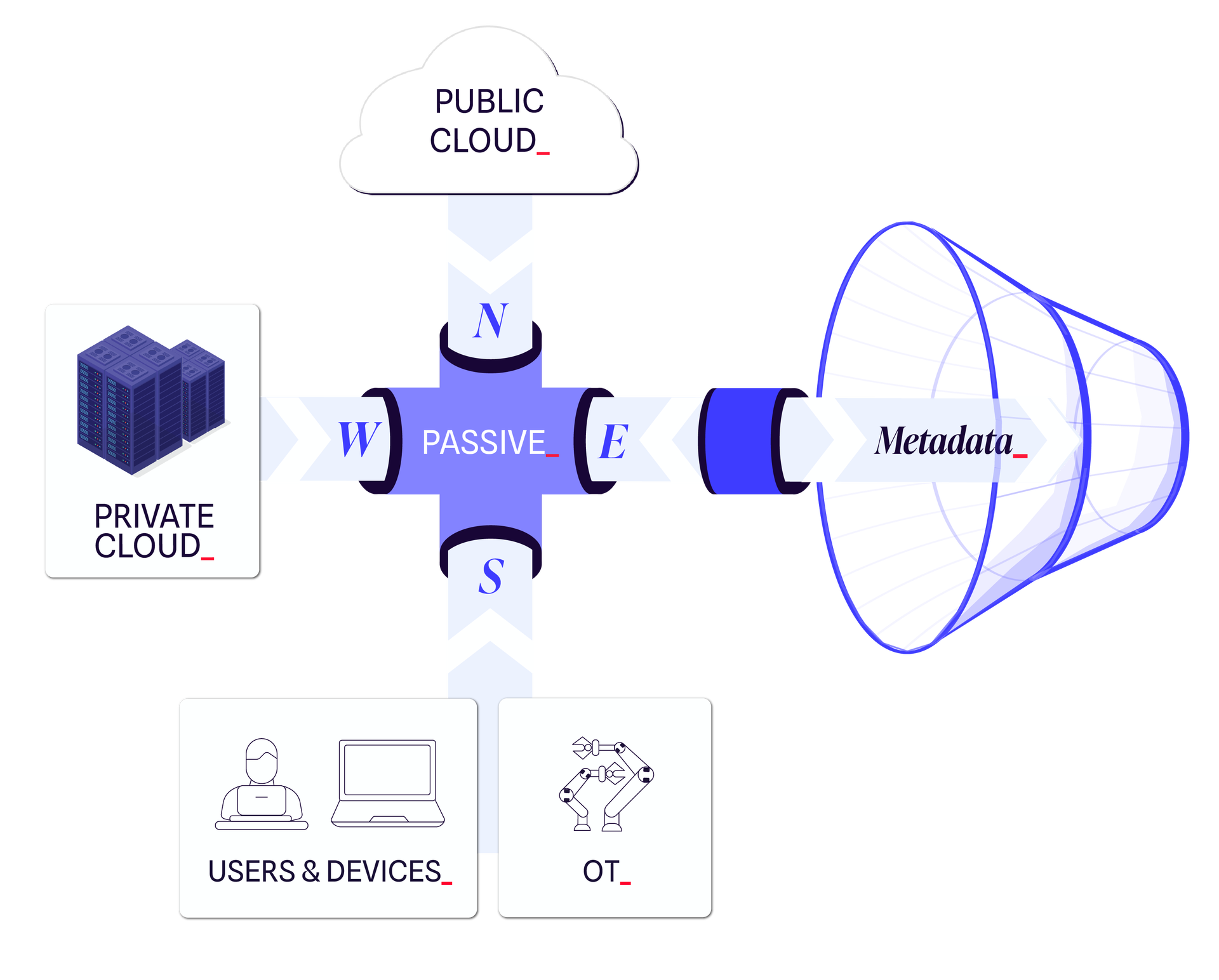
Multi-Source Network Capture
Designed for critical, constrained, and heterogeneous environments (IT, OT, Cloud), Gatewatcher SENSOR provides continuous, passive, and sovereign network observation, ensuring that detection, decision, and response capabilities are grounded in irrefutable data.
Without reliable sensors, cybersecurity becomes speculative. Gatewatcher ensures that visibility remains accurate, consistent, and aligned with real-world operational constraints and business objectives.
Precise visibility into your network traffic
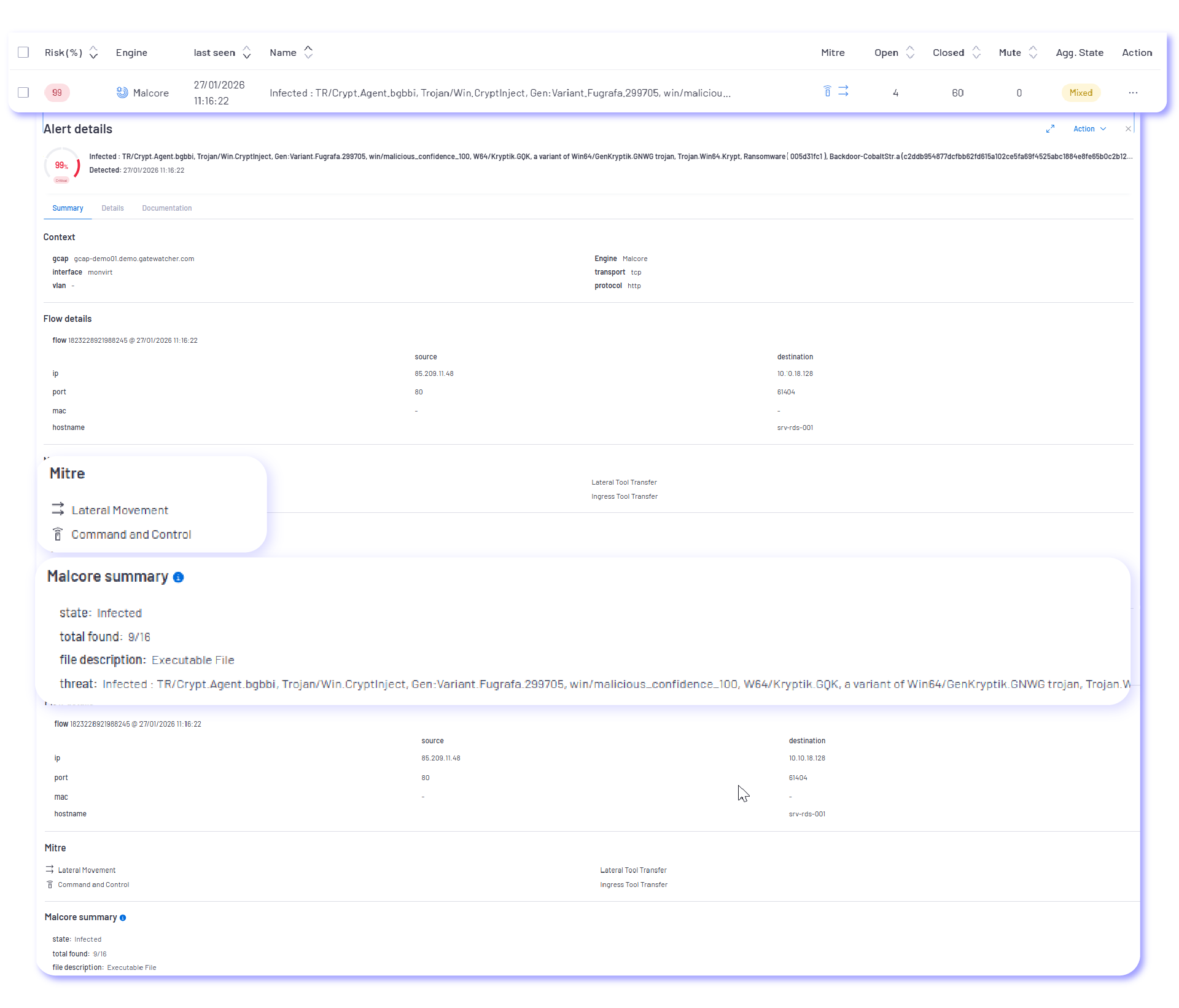
Alerts surface weak threat signals and exposed assets, providing clear, actionable visibility to accelerate decision-making and response.
SENSOR key features:
- Passive, exhaustive, high-performance network traffic collection
- Visibility into endpoint, user, and application activity through deep packet inspection (DPI)
- Flow normalization to ensure data integrity and traceability
- Simple deployment with no agents and no impact on existing infrastructures
- Hybrid operation, supporting both hardware-based and virtual deployments
Your business advantages
By deploying SENSOR, organizations establish a foundation of trust that is essential to protecting their critical activities. By providing factual, independent, and long-lasting visibility into the network, SENSOR enables security to be grounded in reliable evidence.
Organizations benefit from:
- An independent network data source, immune to endpoint compromise or manual manipulation
- Immutable and indisputable evidence, usable during crisis situations or investigations
- Clear reconstruction of events, timelines, and attacker behaviors
- A stronger audit and compliance posture, based on verifiable facts
- Reinforced compliance with regulatory frameworks such as NIS 2 and DORA
Our NDR Platform
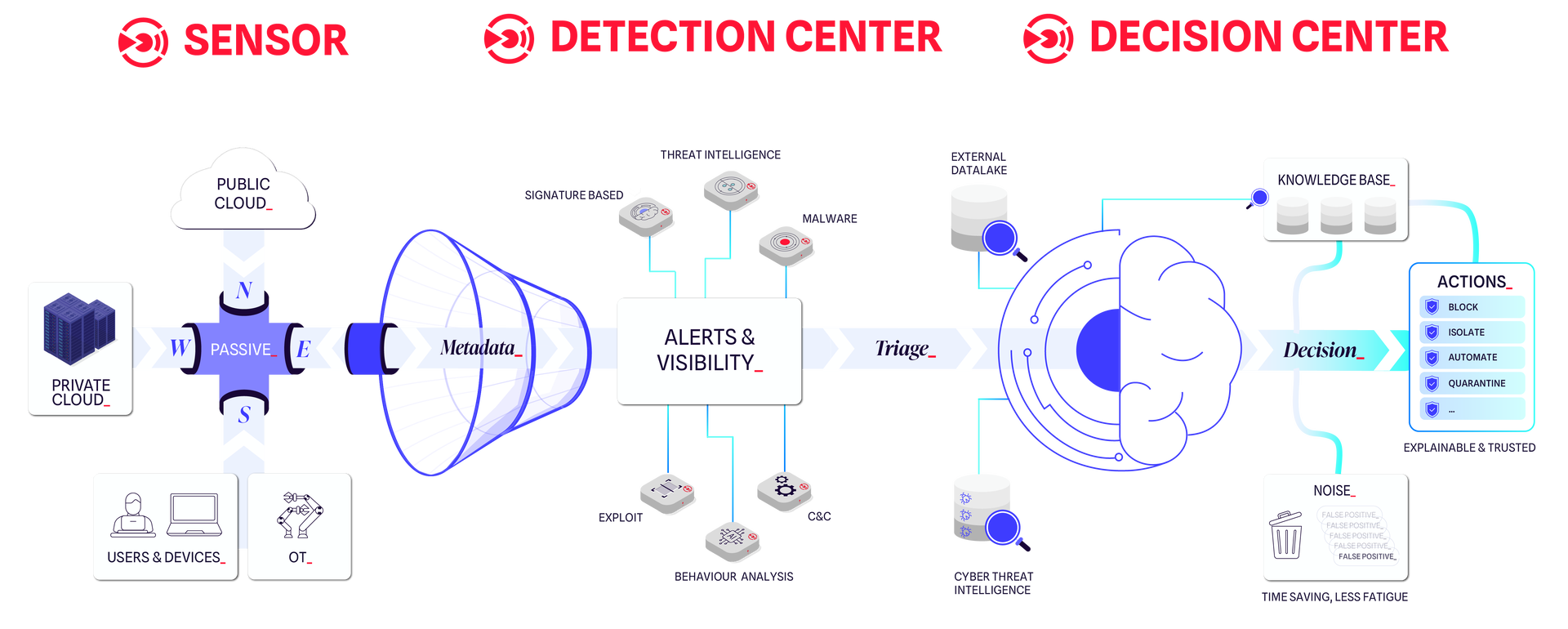
Explore our NDR Platform
DETECTION CENTER
DECISION CENTER
They have already adopted our NDR Platform
Certification







Our Use Case
The essentials of NDR in a practical guide for CISO and CIO