Barometer
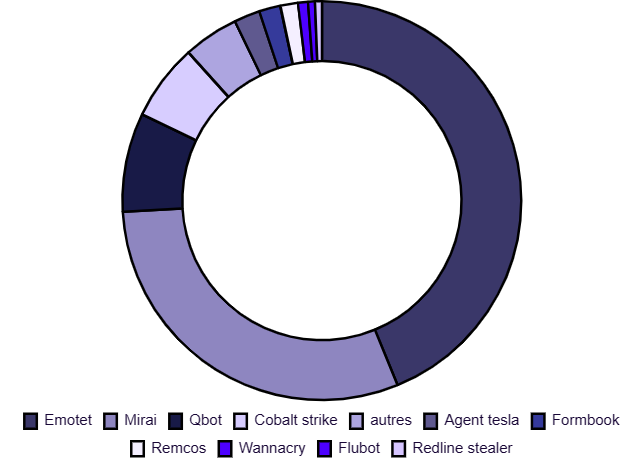
Indicateurs de compromission (IOCs) identifiés
Rapports de compromission identifiés (regroupement d’IoCs)
HIGHLIGHT OF THE MONTH
This month, let’s shed some light on REvil, which has been back in the news for a few weeks. Also known as Sodinokibi, REvil (a contraction of Ransomware and Evil) is a malware that gives its name to a group of Russian-speaking cybercriminals.
Like Conti, which we wrote about in April, the REvil organization was known for its Ransomware-as-a-Service model. From the similarity of their code, the group appeared to be the successor to GandCrab, a RaaS responsible for more than €300 million in losses and the infection of more than 500,000 victims worldwide before their voluntary shutdown in late 2019, according to the FBI.
REvil/Sodinokibi first appeared in April 2019 and quickly gained popularity, becoming one of the most reported malware to ANSSI french agency over the course of 2020. In late October 2021, following the disabling of their infrastructure by a multinational operation, including the FBI and Secret Service for the United States, the organization was shut down. The Russian intelligence bureau then proceeded in January 2022 to arrest suspected REvil members.
However, since the beginning of April 2022, the group is back in the news. Security researchers have found clues to its resurrection: the website ‘Happy Blog’ has appeared on a Russian BitTorrent link platform and redirects to the page REvil used to publish information about its targets. The list of victims has been updated with two new names, including the Oil India group, which confirmed that it was targeted by ransomware on April 10. However, the return of the original group has not been confirmed yet.

TOP
TOP
DEFINITION OF THE MONTH
MITRE ATT&CK, which stands for “MITRE Adversarial Tactics, Techniques, and Common Knowledge” is a framework created in 2013 by MITRE, a U.S. nonprofit organization.
It is a knowledge base that concentrates the TTPs (for Tactics, Techniques & Procedures) used by malicious actors. These are arranged in categories that represent the stages of the killchain. Each tactic groups together several techniques, documented by a page in the repository, with an identifier, a definition and a list of countermeasures.
There are three matrices of tactics that contain techniques specific to the platforms concerned: Enterprise, for classic enterprise OS and tools (Windows, Linux and/or MacOS), Mobile for Android and IOS platforms, and ICS (Industrial Control Systems) for industrial production infrastructures. This separation aims to describe each case more effectively, because an attack takes place differently depending on the platform
The MITRE repository aims to facilitate the analysis of malware, the writing and reading of technical documents by providing a common and standardized basis to categorize the steps and techniques used in any cyber-attack, assessing their severity, their technical complexity. The repository also simplifies the implementation of defense and detection strategies by highlighting exploited vulnerabilities in system.

TOP

TOP
ABOUT THE CYBER THREATS BAROMETER
Malware, zero-day vulnerabilities, advanced persistent threats, industries and sectors particularly targeted, weak signals of emerging attacks…It’s no secret that knowledge of one’s adversary is a key factor for the security of an enterprise. The Cyber Threats Barometer gives you a monthly overview of the cyber threats detected in the previous month by Gatewatcher CTI , our Cyber Threat Intelligence platform.
Gatewatcher CTI’s automated collection, analysis and correlation engines are continuously fed by more than three thousand data sources from multiple channels: social networks, specialized sites, dark and deep web. They make threat information available an average of 24 hours in advance of the competition and help operational response teams make better decisions by dramatically reducing their analysis and incident treatment times.