SmartLoader : Large-scale infiltration via GitHub uncovered by Gatewatcher’s Purple Team
Hundreds of GitHub repositories, a harmless-looking scripting language, and a meticulously orchestrated attack.
Behind seemingly innocent repositories hides SmartLoader, a highly effective multi-stage loader. Our Purple Team investigated: a deep technical dive into an attack scheme where legitimacy becomes the weapon of choice.

Discover more in the analysis
SmartLoader: A malicious campaign hijacking GitHub and generative AI to bypass cybersecurity mechanisms.
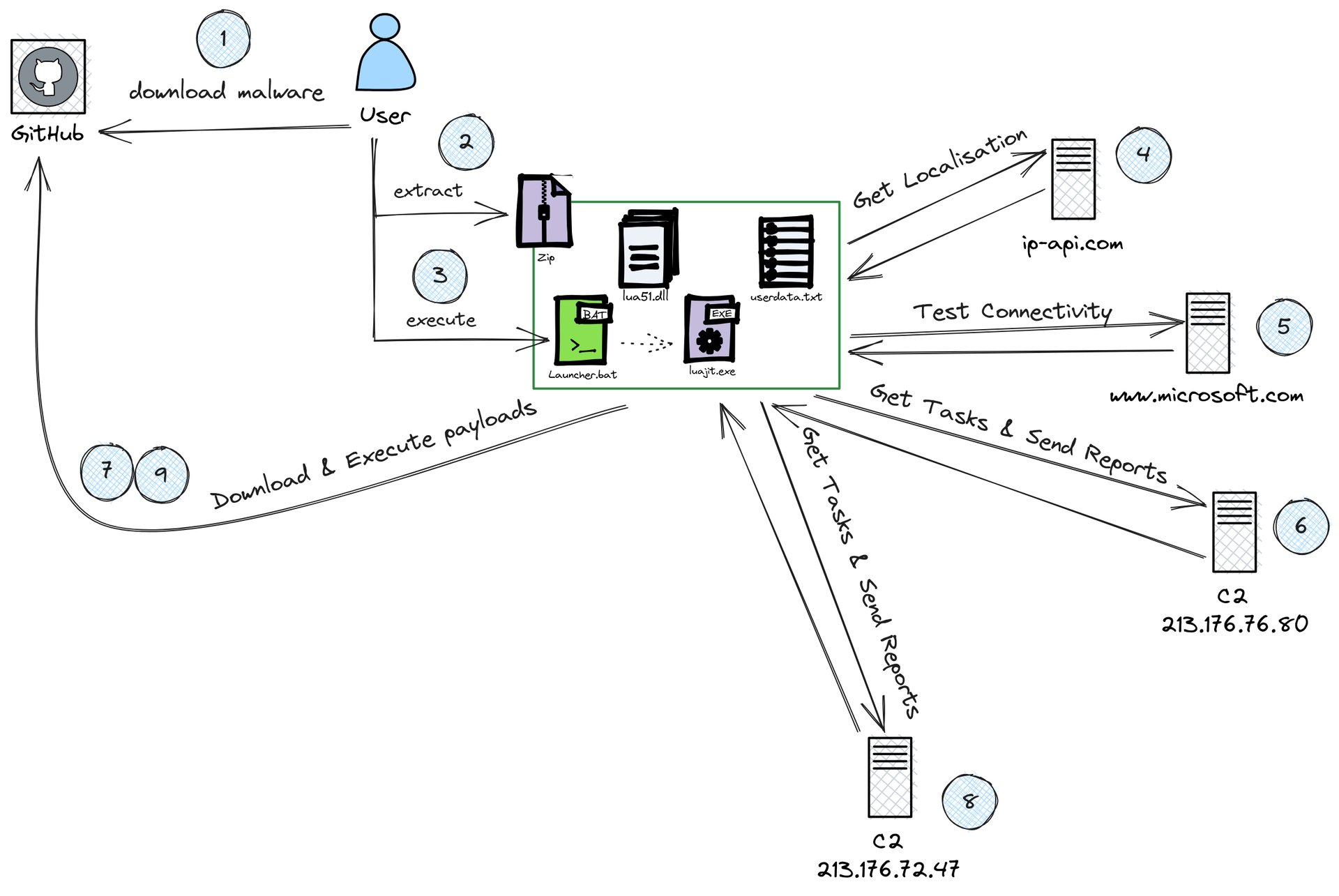
Analyzed by Gatewatcher’s Purple Team, SmartLoader relies on public GitHub repositories and the automation of legitimate scripts to deliver multi-stage malicious payloads. The investigation reveals the combined use of LuaJIT, AutoIT, and environment detection techniques to ensure persistence and evade sandboxes.
The report also highlights the use of generative AI to craft credible READMEs, consistent GitHub profiles, and large-scale automated commits – a silent evolution of the threat that complicates detection for SOC teams and traditional security solutions.
Summary
Part 1 : Hidden in plain sight_
1.1 INVENTORY
1.2 STRAINS
Part 2 : Analysis_
2.1 OBSERVATION
2.2 RECONNAISSANCE
2.3 COMMAND & CONTROL
2.4 STAGE 2
2.5 THE FINAL LOADER
Part 3 : Detection_
3.1 SIGFLOW
Conclusion_
IOCs_
Find out more



